Difference between revisions of "BOINC Security"
(→Virtual Machine-based sandboxing: changing position of word 'five') |
(removing superfluous breaks) |
||
| Line 10: | Line 10: | ||
<br> | <br> | ||
== Code signing == | == Code signing == | ||
| − | |||
Suppose you volunteer for a project, and hackers break into that project's server and replace its programs with malware. Will the malware be downloaded and run on your PC? | Suppose you volunteer for a project, and hackers break into that project's server and replace its programs with malware. Will the malware be downloaded and run on your PC? | ||
<br> | <br> | ||
| Line 24: | Line 23: | ||
<br> | <br> | ||
== Account-based sandboxing == | == Account-based sandboxing == | ||
| − | |||
BOINC's second line of defense is called '''account-based sandboxing'''. Operating systems (Windows, Mac OS X, Linux) have a notion of '''user accounts'''. Each file and running program is associated with a user account. An '''unprivileged account''' is one that has access only to its own files; a program running under such an account is not able to access or modify any other data on the computer.<br> | BOINC's second line of defense is called '''account-based sandboxing'''. Operating systems (Windows, Mac OS X, Linux) have a notion of '''user accounts'''. Each file and running program is associated with a user account. An '''unprivileged account''' is one that has access only to its own files; a program running under such an account is not able to access or modify any other data on the computer.<br> | ||
<br> | <br> | ||
| Line 31: | Line 29: | ||
<br> | <br> | ||
== Virtual Machine-based sandboxing == | == Virtual Machine-based sandboxing == | ||
| − | |||
An even stronger form of sandboxing is provided by a technology called '''virtual machines'''. Programs running in virtual machines cannot access any files on your computer.<br> | An even stronger form of sandboxing is provided by a technology called '''virtual machines'''. Programs running in virtual machines cannot access any files on your computer.<br> | ||
<br> | <br> | ||
| Line 38: | Line 35: | ||
== Rogue and spoof projects == | == Rogue and spoof projects == | ||
| − | |||
The BOINC server software is freely available; anyone can use it. So hackers can create BOINC projects of two sorts:<br> | The BOINC server software is freely available; anyone can use it. So hackers can create BOINC projects of two sorts:<br> | ||
* '''Rogue projects''': the web site claims to do good-of-humanity research, but its programs are malware. | * '''Rogue projects''': the web site claims to do good-of-humanity research, but its programs are malware. | ||
| Line 52: | Line 48: | ||
<br> | <br> | ||
== Client download security == | == Client download security == | ||
| − | |||
The above mechanisms assume that your BOINC client software is valid. What if hackers break into the BOINC server and replace the BOINC installers with malware?<br> | The above mechanisms assume that your BOINC client software is valid. What if hackers break into the BOINC server and replace the BOINC installers with malware?<br> | ||
On Windows, you are protected from this by another form of code signing. When you run the BOINC installer on Windows, the first thing you should see is:<br> | On Windows, you are protected from this by another form of code signing. When you run the BOINC installer on Windows, the first thing you should see is:<br> | ||
| Line 68: | Line 63: | ||
<br> | <br> | ||
== Building your own software == | == Building your own software == | ||
| − | |||
For the ultimate in security, you can build everything yourself.<br> | For the ultimate in security, you can build everything yourself.<br> | ||
<br> | <br> | ||
Revision as of 14:29, 28 September 2016
BOINC downloads programs over the Internet and runs them on your PC. You may be concerned that BOINC could be exploited by hackers to run malware on your PC. ("malware" is software that does malicious things such as stealing private data).
Is BOINC safe? The short answer: in practice, yes. After 13 years, running on millions of PCs, there have been no security incidents due to BOINC.
However, the lack of incidents does not mean that none are possible. All software has security risks, and BOINC is no exception.
We will now explain:
- How BOINC eliminates the most obvious risks.
- How you can reduce the remaining risks.
Code signing
Suppose you volunteer for a project, and hackers break into that project's server and replace its programs with malware. Will the malware be downloaded and run on your PC?
BOINC uses a mechanism called code signing that makes this impossible, as long as projects use proper practices.
Code signing is based on *public-key cryptography*. Each project has a code-signing key pair consisting of a public key and a private key. The public is sent to your client when you add the project. The private key is used to create "signatures" for programs. The BOINC client will only run programs with valid signatures.
Projects are instructed to keep the private key only on a computer that is never connected to a network, and that is physically secure. This computer is used to create signatures. As long as these instructions are obeyed, hackers cannot sign malware, even if they break into the project's server. Therefore they cannot trick BOINC into running malware.
Most BOINC projects follow these practices. However, some projects are lazy and keep their code-signing key on network-connected computers. This undermines the mechanism.
So, if you're concerned about security (and you should be!) don't attach to a project unless it can convince you that it follows the code-signing procedure correctly. Ask project administrators to describe how they do code signing.
Account-based sandboxing
BOINC's second line of defense is called account-based sandboxing. Operating systems (Windows, Mac OS X, Linux) have a notion of user accounts. Each file and running program is associated with a user account. An unprivileged account is one that has access only to its own files; a program running under such an account is not able to access or modify any other data on the computer.
BOINC can be configured to use account-based sandboxing - that is, to run project applications under an unprivileged account. This is the default on Android, Mac OS X and on the installers provided by Linux distributions.
Currently, it is not the default on Windows because GPU applications can't run under unprivileged accounts. However, you can enable it on Windows by checking the Protected execution mode or Service install box during installation (depending on the version of BOINC).
Virtual Machine-based sandboxing
An even stronger form of sandboxing is provided by a technology called virtual machines. Programs running in virtual machines cannot access any files on your computer.
Currently five projects use this technique.
Rogue and spoof projects
The BOINC server software is freely available; anyone can use it. So hackers can create BOINC projects of two sorts:
- Rogue projects: the web site claims to do good-of-humanity research, but its programs are malware.
- Spoof projects: the web site mimics that of an established project, but its programs are malware.
BOINC provides some protection again rogue and spoof project: the projects shown in the BOINC Manager's Add Project wizard are known to us (the BOINC project) to be legitimate.
However, if you add a project not on this list (by entering its URL in the form) it's up to you make sure it's legitimate.
Some things you can do to check:
- If a project claims to be academic, its URL should be in the .edu domain (or its equivalent outside the U.S.).
- If a project claims to be from an institution such as a university, you can contact the institution to verify this.
- Go on the BOINC message boards, see what other people say about the project, and see how long it's been operating.
Client download security
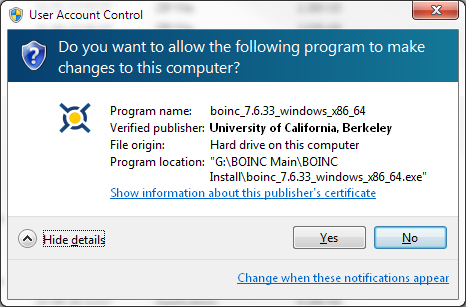
The above mechanisms assume that your BOINC client software is valid. What if hackers break into the BOINC server and replace the BOINC installers with malware?
On Windows, you are protected from this by another form of code signing. When you run the BOINC installer on Windows, the first thing you should see is:
(Note: the version number may be different).
This verifies that the installer is valid.
On Mac OS 10.8 and later, you can select your security settings in system preferences to allow running only applications from the App store or those signed by trusted developers
registered with Apple. BOINC installers for the Mac are code signed with credentials provided by Apple, so OS X will accept them after warning you they have
been downloaded from the Internet (as long as you have set your security preferences in this way.)
On Linux, code signing is not used.
Building your own software
For the ultimate in security, you can build everything yourself.
BOINC is open source software. You can download the source code, inspect it, then build it for your computer.
In addition, many BOINC-based projects make their application source code available. You can download and inspect the source code from their web site, build it for your computer, then use
BOINC's Anonymous platform system to run the resulting executables from the BOINC client.